In the wireless generation, traffic was transmited via air, it mask more easy to capture those packet.
However, according to IEEE802.11i, data type packet was encrypted by WPA/ WPA2 encryption.
If we want to peek the plaintext of those encrypted traffic, we should capture 4-way handshake and calculate the correct PTK.
Currently there are the following methods can crack WPA2 encryption
- Dictionary attack
- KRACK
key reinstall loophole was fixed after hostaps2.8 or abvoe. - Using
PMKID
For simplicity, wireless peeker used Dictionary attack to get the PTK between AP and victim.
However, Simplicity means stupid, this attack should take a lot of time to test all password in dictionary.
All decrypted taffic will be storaged on pcapng format file by sprcify file name with -w flag.
- Modify
crossitem inMakefileto cross-compile if you need. - Just type
Make
MITM:
The main process which can crash wpa2 password, calculate ptk, decrypte wireless packet and store those packet.MITM_cil:
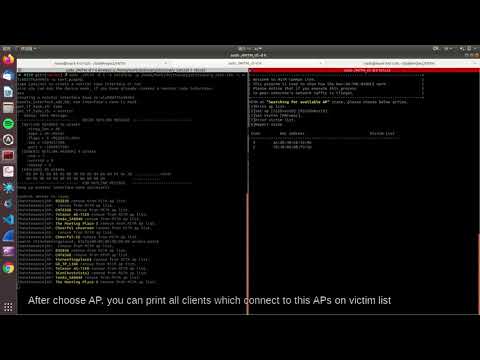
The process which can interaction withMITMprocess, like set ap and victim you want to hack, report some information of network...
This project just used to show how attack work, please do not use it to do anything illegel.